Supermicro 中心是企业级计算、存储、网络及绿色计算技术领域的全球领导者Supermicro产品安全更新与信息的重要渠道。我们致力于持续改进安全实践。
客户安全始终是我们的首要任务,因此我们已采取多项措施Supermicro 运行安全。 当今服务器与存储系统日益多功能化,其复杂性与安全需求同步提升。面对威胁行为者Supermicro 构建防御机制以保护用户与客户,从而将我们的安全技术推向行业巅峰。Supermicro 客户期望部署符合高安全标准的产品,因此我们的解决方案旨在提供最高级别的防护保障。
Supermicro 您遵循安全最佳实践,包括保持操作系统更新,并运行最新版本的固件和所有软件。
生命周期网络安全产品保护
Supermicro 专为美国制造的服务器产品。通过将生产集中于美国工厂,确保了系统完整性。这些"美国制造"的产品降低了外国网络安全入侵的风险,并面向全球客户供应。欲了解更多详情,请访问美国制造解决方案页面。
Supermicro 整个供应链体系的网络安全实践,采取更广泛的"从摇篮到坟墓"方法,确保产品从采购、生产、运行直至自然报废的全生命周期安全。
Supermicro的最佳实践旨在满足其产品安全要求,这些要求由丰富的安全功能和特性提供支持。这些特性确保客户能够确Supermicro符合行业安全标准。
最后更新
Supermicro 您数据中心的安全性Supermicro 重中之重。Supermicro 新发布的 X14/H14 以及 X13/H13和X12/H12系列服务器及存储系统。这些内置功能将为您的数据中心建立安全运营提供指导。请参阅以下列表。
| 类别 | 安全规格 | 英特尔 X14 产品 | AMD H14 产品 | 英特尔 X13 产品 | AMD H13 产品 | 英特尔 X12 产品 | AMD H12 产品 |
|---|---|---|---|---|---|---|---|
| 硬件 | 信任的硅根 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| 机箱入侵保护 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| 可信平台模块(TPM)2.0 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| BMCTPM1 | ✔ | ✔ | ✔ | ✔ | |||
| 英特尔启动保护 | ✔ | ✔ | ✔ | ||||
| 英特尔® 软件防护扩展(英特尔® SGX)1 | ✔ | ✔ | ✔ | ||||
| AMD 安全处理器 | ✔ | ✔ | ✔ | ||||
| AMD 安全内存加密 (SME) | ✔ | ✔ | ✔ | ||||
| AMD 安全加密虚拟化(SEV) | ✔ | ✔ | ✔ | ||||
| BIOS/BMC | 安全启动 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| 安全驱动器擦除 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| 安全闪存 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| 安全固件更新 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| 加密签名固件 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| 安全红鱼应用程序接口3 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| 密码安全 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| 启用/禁用 USB 动态功能 | ✔ | ✔ | |||||
| 硬盘密码 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| BMC 唯一密码 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| 自动固件恢复 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| 防回滚 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| 运行时 BMC 保护 | ✔ | ✔ | ✔ | ✔ | |||
| 系统锁定 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| 供应链安全:远程认证 | ✔ | ✔ | ✔ | ✔ | |||
| 驱动器密钥管理(超级守护者) | ✔ | ✔ | ✔ | ✔ | |||
| IPMI 2.0 用户锁定 | ✔ | ✔ | ✔ | ✔ | |||
| 安全状态监控 | ✔ | ✔ | ✔ | ✔ | |||
| 安全协议和数据模型(SPDM)管理2 | ✔ | ✔ | ✔ | ✔ | |||
| 标准 | NIST SP 800-193 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| NIST SP 800-147b | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | |
| NIST SP 800-88 | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
备注
- 某些功能可能不适用于所有产品。
- 1在特定型号和配置上
- 2计划于 2024 年第四季度完成
- 3支持 TLS v1.2 / v1.3。支持 RMCP+ 密码套件3 / 17
底板管理控制器(BMC)为不同地点的多个用户提供联网远程访问。BMC 允许系统管理员远程监控系统健康状况和管理计算机事件。BMC 与(智能平台管理接口)IPMI 管理工具一起使用,可以集中控制和监控服务器。BMC 具有多种安全功能,可满足客户的各种要求。

在数据中心管理启用了 BMC 功能的服务器的安全最佳实践
利用认证程序进行动态系统验证
使用系统鉴定检测硬件和固件的任何变化
加密签名的 BMC 固件
了解对BMC 固件和 BIOS 进行加密签名的安全功能
BMC 独特的密码安全功能
了解如何从BMC 独特密码中获益
AMD 安全公告 AMD-SB-7059,2026 年 2 月
Supermicro 已知悉此安全问题,即客户虚拟机 (VM) 可能导致宿主系统崩溃。AMD 已发布针对此漏洞的缓解措施。此漏洞影响 Supermicro H11、H12、H13 和 H14 产品中的 BIOS。
- CVE-2023-31364
英特尔平台更新(IPU)2026.1版,2026年2月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X11、X12 和 X13、X14 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- 英特尔-SA-01314 – 2025.4 IPU - 英特尔® TDX 模块咨询公告
- 英特尔安全公告-01315 – 2026.1 IPU - 英特尔® 芯片组固件安全公告
- 英特尔安全公告-01396 – 2026.1 IPU - 英特尔® 处理器固件安全公告
- INTEL-SA-01397 – 2026.1 IPU - 英特尔®可信域扩展(Intel® TDX)模块安全公告
AMD 安全公告 AMD-SB-3023,2026 年 2 月
Supermicro 已知悉 AMD EPYC™ 处理器平台中存在的潜在漏洞,这些漏洞影响 I/O 内存管理单元 (IOMMU)、AMD 安全加密虚拟化 – 安全嵌套分页 (SEV-SNP) 以及在内部和第三方审计中发现的其他平台组件。此漏洞影响 Supermicro H11、H12、H13 和 H14 产品中的 BIOS。
- CVE-2025-52533, CVE-2025-29950, CVE-2024-36355, CVE-2025-29939, CVE-2025-0012, CVE-2025-52536, CVE-2024-21961, CVE-2025-29948, CVE-2024-21953, CVE-2025-29952, CVE-2025-52534, CVE-2025-54514, CVE-2025-48517, CVE-2025-0031, CVE-2024-36310, CVE-2025-29946, CVE-2025-48514, CVE-2025-0029, CVE-2025-48509
微软安全启动证书颁发机构2011终止服务:向2023证书过渡
微软安全启动CA 2011证书将于2026年6月到期,此后仅依赖该证书的设备将停止接收Windows启动管理器和安全启动组件的安全更新,从而增加启动套件漏洞风险。 微软正过渡至2023年新证书;Supermicro 发布支持性BIOS更新。用户应保持安全启动功能启用状态,安装最新BIOS/固件并应用所有更新——多数系统无需立即操作,因受支持设备将自动完成过渡。
查看详情AMD 安全公告 AMD-SB-3027,2026 年 1 月
Supermicro 此安全问题:过期RLB条目可能导致安全嵌套分页(SNP)的活动虚拟中央处理器(vCPU)复用其他虚拟机(VM)的TLB条目,从而可能危及数据完整性。AMD 针对此漏洞AMD 缓解措施。该漏洞影响Supermicro H14产品的BIOS。
- CVE-2025-29943
Supermicro 漏洞,2025年11月
在部分supermicro 和CMM中发现了四个安全问题。这些问题可能影响Supermicro 固件。
- CVE-2025-7623
- CVE-2025-8076
- CVE-2025-8404
- CVE-2025-8727
AMD 安全公告 AMD-SB-3029,2025 年 11 月
Supermicro 此安全问题:过期RLB条目可能导致安全嵌套分页(SNP)活动虚拟中央处理器(vCPU)复用其他虚拟机(VM)的TLB条目,从而可能危及数据完整性。AMD 为此漏洞AMD 缓解措施。该漏洞影响Supermicro 、H13和H14产品的BIOS。
- CVE-2025-29934
AMD 安全公告 AMD-SB-7055,2025 年 10 月
Supermicro 该安全问题,该问题可能导致RDSEED指令以不符合随机性的频率返回"0",同时错误地发出成功信号(CF=1),这可能将失败误判为成功。AMD 针对此漏洞AMD 缓解措施。该Supermicro HSupermicro 产品的BIOS。
- CVE-2025-62626
AMD 安全公告 AMD-SB-3020,2025 年 10 月
Supermicro 安全漏洞,恶意虚拟机监控程序可能在安全嵌套分页(SNP)初始化过程中破坏反向映射表(RMP)。该漏洞AMD 第三、第四及第五代处理器,并Supermicro 、H13和H14系列产品的BIOS系统。
- CVE-2025-0033
英特尔平台更新(IPU)更新 2025.2 第 2 部分,2025 年 8 月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X11、X12 和 X13、X14 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- INTEL-SA-01245- 2025.2 IPU - 英特尔® TDX 模块咨询
- INTEL-SA-01249- 2025.2 IPU - 英特尔®处理器流高速缓存建议
英特尔平台更新(IPU)2025.3 更新,2025 年 8 月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X11、X12 和 X13、X14 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- INTEL-SA-01280- 2025.3 IPU - 英特尔® 芯片组固件咨询
- INTEL-SA-01312- 2025.3 IPU - 英特尔® TDX 模块咨询
- INTEL-SA-01313- 2025.3 IPU - 英特尔® 至强® 处理器固件咨询
AMD 安全漏洞,2025 年 8 月
此更新适用于采用第 1 代/
- AMD-AMD 客户端漏洞 - 2025 年 8 月
- AMD-AMD 服务器漏洞 - 2025 年 2 月
AMD 安全公告 AMD-SB-7029,2025 年 7 月
AMD Supermicro 态执行安全漏洞。AMD 调查微软题为《进入、退出、页面故障、泄露:测试微架构泄露的隔离边界》AMD 若干侧信道攻击。
- CVE-2024-36348
- CVE-2024-36349
- CVE-2024-36350
- CVE-2024-36357
2025.1 IPU - 英特尔® 处理器咨询,INTEL-TA-01209,2025 年 6 月
Supermicro 该安全漏洞:未经专业培训的用户通过本地操作系统访问进行身份验证后,可能利用英特尔® PTT固件中的英特尔® CSME和英特尔® SPS固件存在的越界读取漏洞实施拒绝服务攻击,从而对系统可用性造成高风险影响。
- CVE-2025-2884
AMD 安全公告 AMD-SB-7039,2025 年 6 月
Supermicro 该安全漏洞,可能允许特权攻击者从x86架构访问加密协处理器(CCP)寄存器。此问题AMD 第一、第二及第三代处理器,以及部分H11和H12代产品。
- CVE-2023-20599
英特尔平台更新(IPU)2025.2 更新,2025 年 5 月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X11、X12 和 X13、X14 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- INTEL-SA-01244- 2025.2 IPU - 英特尔® 处理器咨询
- INTEL-SA-01247- 2025.2 IPU - 英特尔®处理器间接分支预测器建议
2025.1 IPU - 英特尔® 处理器咨询,INTEL-TA-01153,2025 年 5 月
处理器事件或预测可能允许不正确的操作(或带有不正确数据的正确操作)瞬时执行,从而可能通过隐蔽通道暴露数据。间接分支预测可能无法完全受制于增强的 IBRS 特性和间接分支预测障碍。此更新适用于由英特尔至强® 和其他英特尔处理器支持的 X11、X12 和 X13 系列产品。
此Supermicro 。Supermicro 任何关于本公告所述漏洞的公开披露或恶意利用情况。
- INTEL-SA-01153 - 2025.1 IPU - 英特尔® 处理器咨询
AMI 安全咨询 AMI-SA-2025003,2025 年 3 月
Supermicro AMI安全公告AMI-SA202503中报告的BIOS固件潜在漏洞。Aptio® V BIOS存在漏洞,攻击者可通过本地手段引发检查时与使用时冲突(TOCTOU)竞态条件。成功利用此漏洞可能导致任意代码执行。
此Supermicro 。Supermicro 任何关于本公告所述漏洞的公开披露或恶意利用情况。
- CVE-2024-54084
AMD 安全公告 AMD-SB-7033,2025 年 3 月
Supermicro 报告的安全问题,即"AMD 签名验证漏洞"。该漏洞源于签名验证算法的缺陷,可能使具备管理员特权的攻击者能够加载任意CPU微代码补丁。
- CVE-2024-36347
英特尔平台更新(IPU)2025.1 更新,2025 年 2 月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X11、X12 和 X13 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- INTEL-SA-01139- 2025.1 IPU - UEFI 固件咨询
- INTEL-SA-01152- 2025.1 IPU - 英特尔® 芯片组固件咨询
- INTEL-SA-01213- 2025.1 IPU - 英特尔® SGX 咨询
- INTEL-SA-01228- 2025.1 IPU - 第 13 和第 14 代英特尔®酷睿™处理器咨询
AMD 安全漏洞,2025 年 2 月
此更新适用于采用第 1 代/
- AMD-AMD 客户端漏洞 - 2025 年 2 月
- AMD-AMD 服务器漏洞 - 2025 年 2 月
AMD 安全公告 AMD-SB-7028,2025 年 2 月
Supermicro Eclypsium报告的系统管理模式(SMM)调用漏洞,该漏洞Supermicro 支持多AMD AmdPlatformRasSspSmm UEFI模块中。此问题AMD 第二代处理器以及H11和H12代产品。
- CVE-2024-21924
AMD 安全公告 AMD-SB-7027,2025 年 2 月
Supermicro 报告的两项安全漏洞,这些漏洞存在于支持AMD AmdPspP2CmboxV2和AmdCpmDisplayFeatureSMM UEFI模块中,可能使攻击者得以在SMM(系统管理模式)内执行代码。该问题影响AMD 第一、第二、第三及第四代处理器,以及H11、H12和H13代产品系列。
- CVE-2024-0179
- CVE-2024-21925
AMD 安全公告 AMD-SB-6016,2025 年 2 月
Supermicro 电源管理固件(PMFW)AMD 管理单元(SMU)存在的安全漏洞。此问题AMD MI300X H13DSG-OM产品。
- CVE-2024-21927
- CVE-2024-21935
- CVE-2024-21936
AMD 安全公告 AMD-SB-6008,2025 年 2 月
Supermicro 电源管理固件(PMFW)AMD 管理单元(SMU)存在的安全漏洞。此问题AMD MI300X H13DSG-OM产品。
- CVE-2024-21971
- CVE-2023-20508
AMD 安全公告 AMD-SB-3019,2025 年 2 月
Supermicro 报告的安全漏洞:具备管理员特权的攻击者可能利用签名验证算法中的缺陷,加载任意CPU微代码补丁,从而导致基于SEV的机密客户机保护机制失效。
- CVE-2024-56161
Supermicro IPMI 固件漏洞,2025年1月
在部分Supermicro 发现了若干安全问题。这些问题影响Supermicro 固件。
- CVE-2024-10237
- CVE-2024-10238
- CVE-2024-10239
AMD 安全公告 AMD-SB-3015,2024 年 12 月
Supermicro 安全漏洞,该漏洞可能导致串行存在检测(SPD)元数据被篡改,使连接的内存模块显示容量大于实际容量,从而引发内存地址别名问题。此AMD 第三代和第四代处理器主板。该Supermicro 系列产品的BIOS。
- CVE-2024-21944
Supermicro IPMI固件漏洞,代号"Terrapin",2024年10月
部分Supermicro 存在安全漏洞。Terrapin漏洞允许攻击者降级安全签名算法并禁用特定安全措施。Terrapin攻击需要攻击者实施主动的中间人攻击。
- CVE-2023-48795
BIOS 漏洞,2024 年 9 月
Supermicro BIOS固件中Supermicro 两个潜在漏洞。这些漏洞可能使攻击者能够写入SMRAM并劫持RIP/EIP指令。该漏洞影响Denverton平台的Supermicro 。Supermicro 任何关于本公告所述漏洞的公开披露或恶意利用情况。
- CVE-2020-8738
- CVE-2024-44075
英特尔平台更新(IPU)2024.3 更新,2024 年 8 月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X11、X12 和 X13 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- INTEL-SA-01038- 2024.2 IPU - 英特尔®酷睿™Ultra 处理器流高速缓存咨询
- INTEL-SA-01046- 2024.2 IPU - 英特尔®处理器流缓存咨询
- INTEL-SA-00999- 2024.3 IPU - 英特尔® 芯片组固件咨询
- INTEL-SA-01083- 2024.3 IPU - SMI 转移监控器建议
- INTEL-SA-01100- 2024.3 IPU - 英特尔® 至强® 处理器咨询
- INTEL-SA-01118- 2024.3 IPU - 第三代英特尔®至强®可扩展处理器咨询
- INTEL-SA-01103- 2024.3 IPU - 英特尔® 处理器 RAPL 接口建议
AMD 安全漏洞,2024 年 8 月
此更新适用于采用第 1/2nd/3rd/4th 代AMD EPYC™ 处理器的 H11、H12 和 H13 系列产品。此更新还适用于采用 Ryzen™ Threadripper™ 处理器的 M11/M12 和 H13 系列产品。在AMD EPYC™ 和AMD Ryzen™ AGESA™ PI 软件包中发现并缓解了各种平台组件中的潜在漏洞。
- AMD-AMD 客户端漏洞 - 2024 年 8 月
- AMD-AMD 服务器漏洞 - 2024 年 8 月
AMD 安全公告 AMD-SB-7014,2024 年 8 月
Supermicro 该安全漏洞:即使启用了SMM锁定功能,具备root权限的攻击者仍可能修改系统管理模式(SMM)的配置。此问题AMD 第一、第二、第三及第四代处理器,以及H11、H12和H13代产品。
- CVE-2023-31315
AMD 安全公告 AMD-SB-3011,2024 年 8 月
Supermicro 以下安全问题:恶意虚拟机管理程序可能在安全加密虚拟化-安全嵌套分页(SEV-SNP)客户机虚拟机退役后对其内存进行解密。该问题AMD 第三代和第四代处理器主板。此漏洞影响Supermicro H13系列产品的BIOS。
- CVE-2023-31355
- CVE-2024-21978
- CVE-2024-21980
PKFAIL:Supermicro 漏洞,2024年7月
Supermicro 名为“PKFAIL”的安全漏洞问题。该新漏洞可能使恶意行为者从操作系统发起高级固件级威胁。经Supermicro 部分Supermicro 平台密钥(PK),这些密钥代表 BIOS 的信任根。这些不安全密钥由 American Megatrends International (AMI) 生成,并作为参考示例提供给Supermicro。
查看详情OpenSSH "regreSSHion" 漏洞,2024 年 7 月
在部分Supermicro BMC固件中,发现了一个名为"regreSSHion"的OpenSSH关键信号处理器竞争条件安全漏洞。该漏洞可能导致未经身份验证的远程代码执行(RCE),并获得root权限。
- CVE-2024-6387
BIOS 漏洞,2024 年 7 月
Supermicro BIOS固件中Supermicro 潜在漏洞。这些漏洞影响特定型号的X11主板。Supermicro 任何关于本公告所述漏洞的公开披露或恶意利用情况。
- CVE-2024-36432
- CVE-2024-36433
- CVE-2024-36434
Supermicro IPMI固件漏洞,2024年7月
在部分Supermicro 中发现了一个安全问题。该问题影响其BMC(板载管理控制器)的Web服务器组件。Supermicro 潜在漏洞可能源于固件中"GetValue"函数的缓冲区溢出,该漏洞是由未对输入值进行检查所导致。
- CVE-2024-36435
AMD 安全公告 AMD-SB-1041,2024 年 6 月
Supermicro 已知悉 AMD SPI 保护功能中存在的潜在弱点。此问题影响 AMD EPYC™ 第一代、第二代和第三代处理器主板。此漏洞影响 Supermicro H11 和 H12 产品中的 BIOS。
- CVE-2022-23829
AMD 安全公告 AMD-SB-4007,2024 年 5 月
Supermicro AMD (驱动执行环境)驱动程序中Supermicro 内存泄漏漏洞,该漏洞可能使具有高权限的用户获取敏感信息。此问题AMD 第三代处理器主板。该漏洞影响Supermicro 系列产品的BIOS。
- CVE-2023-20594
- CVE-2023-20597
英特尔平台更新(IPU)更新 2024.2,2024 年 5 月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X13 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- INTEL-SA-01036- 2024.2 IPU - 英特尔® TDX 模块软件建议
- INTEL-SA-01051- 2024.2 IPU - 英特尔® 处理器咨询
- INTEL-SA-01052- 2024.2 IPU - 英特尔®酷睿™Ultra 处理器咨询
Supermicro 漏洞,2024年4月
在部分Supermicro 发现了若干安全漏洞。这些问题(跨站脚本攻击和命令注入)可能Supermicro IPMI(Web UI)的Web服务器组件。已发布更新的BMC固件以缓解这些潜在漏洞。
- SMC-2024010010(CVE:CVE-2024-36430)
- SMC-2024010011(CVE:CVE-2024-36431)
- SMC-2024010012(CVE:CVE-2023-33413)
英特尔平台更新 (IPU) 更新 2024.1 和 INTEL-TA-00986,2024 年 3 月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X11、X12 和 X13 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- INTEL-SA-00898- 2024.1 IPU - 英特尔®凌动®处理器咨询
- INTEL-SA-00923- 2024.1 IPU - 英特尔® 芯片组软件和 SPS 建议
- INTEL-SA-00929- 2024.1 IPU - BIOS 建议
- INTEL-SA-00950- 2024.1 IPU OOB - 英特尔® 处理器咨询
- INTEL-SA-00960- 2024.1 IPU - 英特尔®至强®处理器咨询
- INTEL-SA-00972- 2024.1 IPU - 英特尔® 处理器总线锁定建议
- INTEL-SA-00982- 2024.1 IPU - 英特尔® 处理器返修预测咨询
- INTEL-SA-00986- 第四代英特尔®至强®处理器咨询
- INTEL-SA-01045- 2024.1 IPU OOB - 英特尔® 至强® D 处理器咨询
AMD 安全公告 AMD-SB-7009,2024 年 2 月
Supermicro AMD 漏洞问题。AMD 第一代、AMD 代、AMD 代及第四代处理器。此漏洞涉及Supermicro 11、H12及部分H13主板。
- CVE-2023-20576
- CVE-2023-20577
- CVE-2023-20579
- CVE-2023-20587
AMD 安全公告 AMD-SB-3007,2024 年 2 月
Supermicro SEV-SNP固件漏洞问题。该AMD 第三代和第四代处理器,涉及Supermicro 及部分H13系列主板。
- CVE-2023-31346
- CVE-2023-31347
PixieFAIL 漏洞,2024 年 1 月
Supermicro BIOS固件中Supermicro 名为"PixieFAIL"的潜在漏洞。在Tianocore EDKII(UEFI的开源实现)的TCP/IP协议栈(NetworkPkg)中发现了多个漏洞。这九个漏洞若通过网络被利用,可能导致远程代码执行、拒绝服务攻击、DNS缓存中毒及/或敏感信息泄露。 PixieFAILSupermicro 特定型号X11、X12、H11、H12、H13及R12Supermicro 。Supermicro 任何公开披露或恶意利用本公告所述漏洞的案例。
- CVE-2023-45229
- CVE-2023-45230
- CVE-2023-45231
- CVE-2023-45232
- CVE-2023-45233
- CVE-2023-45234
- CVE-2023-45235
- CVE-2023-45236
- CVE-2023-45237
LogoFAIL 漏洞,2023 年 12 月
Supermicro BIOS固件中Supermicro 一个名为“LogoFAIL”的潜在漏洞。 由于BIOS使用的图像解析库存在输入验证不足的问题,特权用户可能通过本地访问实现权限提升。LogoFAIL漏洞Supermicro 特定型号的X11、X12、X13、H11、M12及R12Supermicro 。Supermicro 任何公开披露或恶意利用本公告所述漏洞的案例。
- CVE-2023-39538
- CVE-2023-39539
Supermicro IPMI 固件漏洞,2023年12月
- CVE-2023-33411:IPMI BMC SSDP/UPnP 网络服务器目录遍历和 iKVM 访问允许重新启动 BIOS
- CVE-2023-33412: IPMI BMC 管理 Web 界面虚拟软盘/USB 远程命令执行
- CVE-2023-33413:IPMI BMC 设备使用硬编码的配置文件加密密钥,允许攻击者制作和上传恶意配置文件包,以获得远程命令执行。
AMD 安全公告 AMD-SB-3005
Supermicro 已知悉 AMD INVD 指令安全漏洞。此问题影响第一代 AMD EPYC™ 处理器(支持 SEV 和 SEV-ES)、第二代 AMD EPYC™ 处理器(支持 SEV 和 SEV-ES)以及第三代 AMD EPYC™ 处理器(支持 SEV、SEV-ES、SEV-SNP)。此漏洞影响 Supermicro H11 和 H12 主板。
- CVE-2023-20592
英特尔平台更新 (IPU) 更新 2023.4 和 INTEL-SA-00950,2023 年 11 月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X11、X12 和 X13 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- INTEL-SA-00924- 2023.4 IPU - BIOS 建议
- INTEL-SA-00950- 英特尔® 处理器咨询
AMD 安全漏洞,2023 年 11 月
此更新适用于采用第 1 代/
- AMD-AMD 客户端漏洞 - 2023 年 11 月
- AMD-AMD 服务器漏洞 - 2023 年 11 月
Supermicro IPMI固件中的漏洞
在部分Supermicro 发现了若干安全漏洞。这些问题(跨站脚本攻击和命令注入)可能Supermicro IPMI(Web UI)的Web服务器组件。已发布更新的BMC固件以缓解这些潜在漏洞。
- CVE-2023-40289
- CVE-2023-40284
- CVE-2023-40287
- CVE-2023-40288
- CVE-2023-40290
- CVE-2023-40285
- CVE-2023-40286
堆栈溢出导致的变量修改
Supermicro 固件中发现一个潜在漏洞。攻击者可通过操纵变量利用该漏洞劫持Supermicro 控制流,从而使具备内核级权限的攻击者实现权限提升,并可能执行任意代码。
- CVE-2023-34853
AMD 安全公告 AMD-SB-7005
Supermicro 返回地址预测漏洞(亦称"INCEPTION")。该漏洞AMD 第三代及第四代处理器,并波及Supermicro H12和H13主板型号。
- CVE-2023-20569
英特尔平台更新(IPU)2023.3 更新,2023 年 8 月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X11、X12 和 X13 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- INTEL-SA-00783- 2023.2 IPU - 英特尔® 芯片组固件咨询
- INTEL-SA-00813- 2023.2 IPU - BIOS 建议
- INTEL-SA-00828- 2023.2 IPU - 英特尔® 处理器咨询
- INTEL-SA-00836- 2023.2 IPU - 英特尔®至强®可扩展处理器咨询
- INTEL-SA-00837- 2023.2 IPU - 英特尔®至强®处理器咨询
AMD 安全公告 AMD-SB-7008
Supermicro 已知悉跨进程信息泄露漏洞,亦称“Zenbleed”。此问题影响 AMD EPYC™ 7002 处理器,亦称 AMD “Zen 2” 处理器。此漏洞影响 Supermicro H11 和 H12 主板。
- CVE-2023-20593
SMTP 通知中的外壳注入
supermicro 存在的漏洞可能影响SMTP通知配置。该漏洞可能允许未经身份验证的恶意行为者操控用户输入(如警报设置中的主题字段),从而导致任意代码执行。
- CVE-2023-35861
服务定位协议 SLP 中的反射式拒绝服务 (DoS) 放大漏洞
服务定位协议(SLP)允许未经验证的远程攻击者注册任意服务。这样,攻击者就可以利用欺骗性 UDP 流量来实施具有显著放大系数的拒绝服务(DoS)攻击。
- CVE-2023-29552
媒体信息:英特尔BootGuard OEM私钥可能已泄露,2023年5月
根据对Supermicro 和使用私钥方式的分析Supermicro 不受影响。
英特尔平台更新(IPU)2023.2 更新,2023 年 5 月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X11、X12 和 X13 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- INTEL-SA-00807- 2023.2 IPU - BIOS 建议
AMD 安全漏洞,2023 年 5 月
此更新适用于采用第 1/2nd/3rd/4th 代AMD EPYC™ 处理器的 H11、H12 和 H13 系列产品。此更新还适用于采用 Ryzen™ Threadripper™ 处理器的 M12 系列产品。在AMD EPYC™ 和AMD Ryzen™ AGESA™ PI 软件包中发现并缓解了各种平台组件中的潜在漏洞。
- AMD-AMD 客户端漏洞 - 2023 年 5 月
- AMD-AMD 服务器漏洞 - 2023 年 5 月
超级医生 5 咨询,2023 年 3 月
研究人员发现Supermicro (SD5)存在一个漏洞,可能允许任何通过Web界面认证的用户在安装了SuperDoctor5(SD5)的系统上远程执行任意命令。
- CVE-2023-26795
英特尔平台更新(IPU)2023.1 更新,2023 年 2 月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X11、X12 和 X13 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- INTEL-SA-00700- 2023.1 IPU - 英特尔® 凌动® 和英特尔® 至强® 可扩展处理器咨询
- INTEL-SA-00717- 2023.1 IPU - BIOS 建议
- INTEL-SA-00718- 2023.1 IPU - 英特尔® 芯片组固件咨询
- INTEL-SA-00730- 2023.1 IPU - 第 3 代英特尔®至强®可扩展处理器咨询
- INTEL-SA-00738- 2023.1 IPU - 英特尔®至强®处理器咨询
- INTEL-SA-00767- 2023.1 IPU - 英特尔® 处理器咨询
稳压器模块 (VRM) 和集成电路 (I²C) 过压/欠压,2023 年 1 月
研究人员在电路板管理控制器(BMC)中发现了一个漏洞,该漏洞可能导致电压变化超出 CPU 的指定工作范围,从而影响正常计算。
- CVE-2022-43309
AMD 安全漏洞,2023 年 1 月
此更新适用于采用第 1/2nd/3rd/4th 代AMD EPYC™ 处理器的 H11 和 H12 系列产品。此更新还适用于采用 Ryzen™ Threadripper™ 处理器的 M12 系列产品。在AMD EPYC™ 和AMD Ryzen™ AGESA™ PI 软件包中发现并缓解了各种平台组件中的潜在漏洞。
- AMD-AMD 客户端漏洞 - 2023 年 1 月
- AMD-AMD 服务器漏洞 - 2023 年 1 月
英特尔平台更新(IPU)2022.3 更新,2022 年 11 月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X11 和 X12 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- INTEL-SA-00610- 2022.3 IPU - 英特尔® 芯片组固件咨询
- INTEL-SA-00668- 2022.2 IPU - BIOS 建议
OpenSSL 咨询,2022 年 11 月
OpenSSL 3.x 至 3.0.6 版本存在严重安全漏洞,可能导致系统崩溃或异常行为。Supermicro 此 OpenSSL 漏洞影响。
- CVE-2022-3786
- CVE-2022-3602
微软视窗安全启动绕过,2022 年 8 月
研究人员在微软的第三方引导加载器中发现了几个漏洞,这些漏洞会影响所有使用 x64 UEFI 安全引导的计算机系统。
- CVE-2022-34301
- CVE-2022-34302
- CVE-2022-34303
英特尔平台更新(IPU)更新 2022.2,2022 年 8 月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X11 和 X12 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- INTEL-SA-00657- 2022.2 IPU - 英特尔®处理器咨询
- INTEL-SA-00669- 2022.2 IPU - 英特尔® 芯片组固件咨询
- INTEL-SA-00686- 2022.2 IPU - BIOS 建议
英特尔平台更新(IPU)2022.1 更新,2022 年 6 月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X10、X11 和 X12 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- INTEL-SA-00601- 2022.1 IPU - BIOS 建议
- INTEL-SA-00613- 2022.1 IPU - 英特尔® 引导保护和英特尔® TXT 咨询
- INTEL-SA-00614- 2022.1 IPU - 英特尔® SGX 咨询
- INTEL-SA-00615- 2022.1 IPU - 英特尔® 处理器 MMIO 陈旧数据咨询
- INTEL-SA-00616- 2022.1 IPU - 英特尔®Xeon 咨询
- INTEL-SA-00617- 2022.1 IPU - 英特尔®处理器咨询
AMD 安全漏洞,2022 年 5 月
此更新适用于采用第 1/2nd/3rd 代AMD EPYC™ 处理器的 H11 和 H12 系列产品。此更新还适用于采用 Ryzen™ Threadripper™ 处理器的 M12 系列产品。在AMD EPYC™ 和AMD Ryzen™ AGESA™ PI 软件包中发现并缓解了各种平台组件中的潜在漏洞。
- AMD-AMD 客户端漏洞 - 2022 年 5 月
- AMD-AMD 服务器漏洞 - 2022 年 5 月
英特尔平台更新(IPU)2021.2 更新,2022 年 2 月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X10、X11 和 X12 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- INTEL-SA-00470- 2021.2 IPU - 英特尔® 芯片组固件咨询
- INTEL-SA-00527- 2021.2 IPU - BIOS 建议
- INTEL-SA-00532- 2021.2 IPU - 英特尔®处理器断点控制流建议
- INTEL-SA-00561- 2021.2 IPU - 英特尔® 处理器咨询
- INTEL-SA-00589- 2021.2 IPU - 英特尔 Atom® 处理器咨询
Supermicroache Log4j漏洞的响应
Supermicro 并加入行业行动,共同缓解由高危漏洞CVE-2021-44228(Apache Log4j 2)引发的风险暴露问题,该漏洞亦被称为"Log4Shell"。同时Supermicro正积极应对CVE-2021-45046(Apache Log4j 2)漏洞及CVE-2021-45105(Apache Log4j 2)漏洞。Supermicro Apache Log4j 1.2版本中存在的CVE-2021-4104及 CVE-2019-17571漏洞。
Supermicro 不受这五个漏洞的影响。唯一受影响的应用程序Supermicro 管理器(SPM)。该问题将在新版Supermicro 管理器(SPM)中得到解决,新版本将尽快发布。新版SPM将搭载Log4j 2.17.0版本。
Log4j 2
- CVE-2021-44228
- CVE-2021-45046
- CVE-2021-45105
Log4j 1.2
- CVE-2019-17571
- CVE-2021-4104
英特尔平台更新(IPU)2021.2 更新,2021 年 11 月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X10、X11 和 X12 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- INTEL-SA-00528- 2021.2 IPU - 英特尔®凌动®处理器咨询
- INTEL-SA-00562- 2021.1 IPU - BIOS 参考代码咨询
AMD 安全漏洞,2021 年 11 月
此更新适用于采用第一代/第二代/第三代AMD EPYC™ 处理器的 H11 和 H12 系列产品。在AMD EPYC™ AGESA™ PI 软件包中发现并缓解了各种平台组件中的潜在漏洞。
- AMD-AMD 服务器漏洞 - 2021 年 11 月
英特尔安全咨询 Intel-SA-00525,2021 年 7 月
- INTEL-SA-00525- 英特尔 BSSA(BIOS 共享 SW 架构)DFT 咨询
Intel-SA-00525 安全公告不影响Supermicro 。
查看详情英特尔平台更新(IPU)2021.1 更新,2021 年 6 月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X10、X11 和 X12 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- INTEL-SA-00442- 2021.1 IPU - 英特尔 VT-d 咨询
- INTEL-SA-00459- 2021.1 IPU - Intel-CSME-SPS-TXE-DAL-AMT-Advisory
- INTEL-SA-00463- 2021.1 IPU - BIOS 建议
- INTEL-SA-00464- 2021.1 IPU - 英特尔处理器咨询
- INTEL-SA-00465- 2021.1 IPU - 英特尔处理器咨询
SupermicroTrickboot漏洞的回应,2021年3月
Supermicro 漏洞问题,该问题仅出现在部分X10 UP主板上。Supermicro 为此漏洞提供缓解方案。
TrickBoot 是TrickBot恶意软件工具集中的一项新功能,能够发现漏洞并使攻击者能够读/写/擦除设备上的 BIOS。
更多信息BIOS 检测到 Linux 操作系统中的 GRUB2 引导加载器漏洞,2020 年 11 月
在 2.06 版之前的 GRUB2 中发现了一个漏洞。攻击者可利用 GRUB2 漏洞劫持和篡改 GRUB 验证过程。BIOS 会检测到这种情况,并发出错误信息停止启动。
- CVE-2020-10713
英特尔平台更新(IPU)2020.2 更新,2020 年 11 月
此更新适用于采用英特尔至强® 和其他英特尔处理器的 X10、X11 和 X12 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- INTEL-SA-00358- 2020.2 IPU - BIOS 建议
- INTEL-SA-00391- 2020.2 IPU - 英特尔® CSME、SPS、TXE 和 AMT 咨询
- INTEL-SA-00389- 2020.2 IPU - 英特尔® RAPL 建议
- INTEL-SA-00390- 英特尔 BIOS 平台示例代码咨询
英特尔每月安全更新,2020 年 9 月
此更新适用于采用英特尔酷睿® 处理器的 X11 和 X12 系列产品。英特尔九月安全更新月报将以前可能单独提供的安全更新合并在一起。
请注意,X10 系列产品不受此公告影响。
- 英特尔-SA-00404--英特尔® AMT 和英特尔® ISM 咨询
英特尔平台更新(IPU)2020.1 更新,2020 年 6 月
此更新适用于采用英特尔至强® 处理器的 X10 和 X11 系列产品。英特尔平台更新 (IPU) 将以前可能单独提供的安全更新合并在一起。
- Intel-SA-00295- Intel® CSME、SPS、TXE、AMT 和 DAL 咨询
- Intel-SA-00320- 特殊寄存器缓冲区数据取样咨询
- Intel-SA-00322- 2020.1 IPU BIOS 咨询
- Intel-SA-00329- 英特尔®处理器数据泄露咨询
- Intel-SA-00260- (更新)Intel® 处理器图形 2019.2 QSR 更新咨询
符合 ErP(生态设计)要求的第 9 部分
Lot 9法规是一套针对企业级服务器等数据存储设备的新产品标准。Supermicro Lot 9合规性Supermicro 欧盟服务器及存储产品的生态设计要求。
查看详情英特尔每月二月安全更新,2020 年 2 月
此更新适用于采用英特尔酷睿® 处理器的 X11 系列产品。英特尔每月二月安全更新合并了以前可能单独提供的安全更新。
- Intel-SA-00307- 权限升级、拒绝服务、信息泄露
英特尔每月 12 月安全更新,2019 年 12 月
此更新适用于采用英特尔至强® 处理器的 X10 和 X11 系列产品。英特尔 12 月安全更新月报合并了以前可能单独提供的安全更新。
- Intel-SA-00289- 英特尔® 处理器电压设置修改建议
- Intel-SA-00317- 虚拟化环境中的意外页面故障咨询
英特尔平台更新(IPU)2019.2 更新,2019 年 11 月
此更新适用于采用英特尔至强® 处理器的 X10 和 X11 系列产品。英特尔平台更新(IPU)将以前可能单独提供的安全更新合并在一起。
- 英特尔-SA-00164- 英特尔®可信执行技术 2019.2 IPU 建议
- Intel-SA-00219- 配备英特尔® 处理器图形 IPU 的英特尔® SGX 2019.2 更新咨询
- Intel-SA-00220- 英特尔® SGX 和英特尔® TXT 咨询
- Intel-SA-00240- 英特尔中央处理器本地权限升级咨询
- 英特尔-SA-00241- 英特尔® CSME、服务器平台服务、可信执行引擎、英特尔® 主动管理技术和动态应用程序加载器 2019.2 IPU 建议
- Intel-SA-00254- 英特尔® 系统管理模式 2019.2 IPU 建议
- Intel-SA-00260- Intel® 处理器图形处理器 2019.2 IPU 建议
- Intel-SA-00270- TSX 事务异步中止咨询
- Intel-SA-00271- 电压调制技术咨询
- Intel-SA-00280- BIOS 2019.2 IPU 建议
BMC/IPMI 安全漏洞更新 2019 年 9 月 3 日
研究人员Supermicro 虚拟媒体功能中发现若干安全相关问题,需通过更新BMC固件予以解决。
CVE-2019-16649
CVE-2019-16650
英特尔季度安全发布 (QSR) 更新 2019.1,2019 年 5 月
此更新适用于采用英特尔至强® 处理器的 X8、X9、X10 和 X11 系列产品。季度安全更新 (QSR) 将以前可能单独提供的安全更新合并在一起。
- Intel-SA-00213(CVE-2019-0089、CVE-2019-0090、CVE-2019-0086、CVE-2019-0091、CVE-2019-0092、CVE-2019-0093、CVE-2019-0094、CVE-2019-0096、CVE-2019-0097、CVE-2019-0098、CVE-2019-0099、CVE-2019-0153、CVE-2019-0170)
- INTEL-SA-00223BIOS 未受影响
- INTEL-SA-00233(CVE-2018-12126, CVE-2018-12127, CVE-2018-12130, CVE-2019-11091)
针对这些问题的 BIOS 更新现已推出。请查看以下受影响产品和必要 BIOS 更新的详细信息。
英特尔季度安全发布 (QSR) 更新 2018.4,2019 年 3 月
此更新仅适用于采用英特尔至强® 处理器的 X11 系列产品。季度安全更新 (QSR) 结合了以前可能单独提供的安全更新。
- Intel-SA-00185(CVE-2018-12188、CVE-2018-12189、CVE-2018-12190、CVE-2018-12191、CVE-2018-12192、CVE-2018-12199、CVE-2018-12198、CVE-2018-12200、CVE-2018-12187、CVE-2018-12196、CVE-2018-12185、CVE-2018-12208)
- Intel-SA-00191(CVE-2018-12201、CVE-2018-12202、CVE-2018-12203、CVE-2018-12205、CVE-2018-12204)
"剧透":关于英特尔处理器投机执行的最新研究文章
查看详情Spectre 和 Meltdown 侧通道投机执行
- 英特尔 SA-00115(CVE-2018-3639、CVE-2018-3640)
- Intel-SA-00088(CVE-2017-5715、CVE-2017-5753、CVE-2017-5754)
- 英特尔-SA-00161(CVE-2018-3615、CVE-2018-3620、CVE-2018-3646)
有关英特尔® 管理引擎 (ME)、英特尔® 服务器平台服务 (SPS) 和英特尔® 可信执行引擎 (TXE) 的英特尔安全漏洞
- Intel-SA-00086(CVE-2017-5705, CVE-2017-5708, CVE-2017-5711, CVE-2017-5712, CVE-2017-5706, CVE-2017-5709, CVE-2017-5707, CVE-2017-571000)
2017 年之前的 BIOS/BMC 固件安全更新
请参见 2017 年之前发布的 "常见漏洞和暴露的固件修复"。
Supermicro 与安全社区合作,识别并强化全产品线的安全防护。Supermicro 发布的CVE解决方案,请查阅相关公告。
查看详情常见安全问题:选择类别 "安全
报告产品安全问题
若您Supermicro 遇到安全问题,请发送电子邮件至supermicro,并提供以下详细信息:
- 产品名称/SKU
- 关于脆弱性的详细报告
- 复制说明
- 任何相关的 CVE
请勿在明文电子邮件中包含任何敏感或机密信息——请使用PGP密钥加密您的消息。Supermicro 安全团队将审核您的报告,并与您联系共同解决问题。
查看详情获取Supermicro产品安全更新资讯
立即订阅
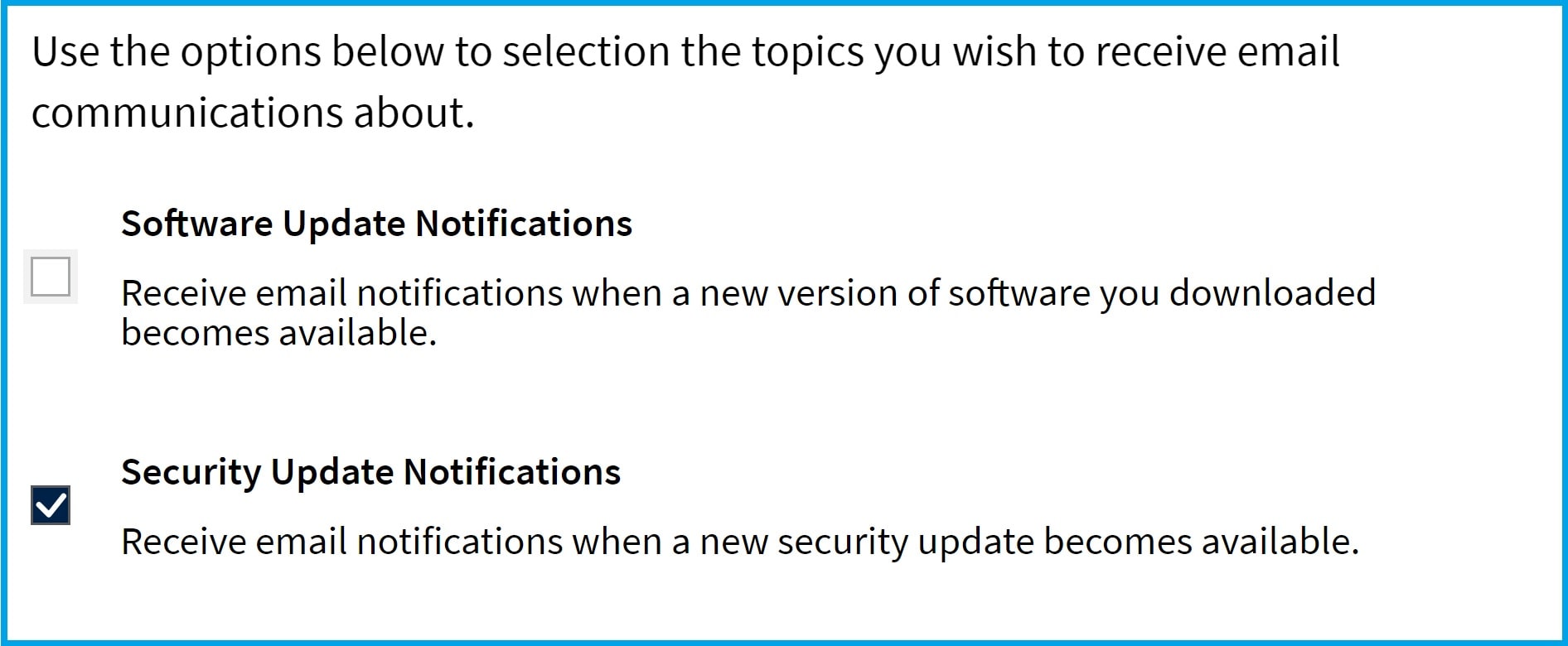
若要订阅Supermicro 警报,请按以下步骤操作:
1.转到屏幕右上角,登录或创建单点登录(SSO)账户:
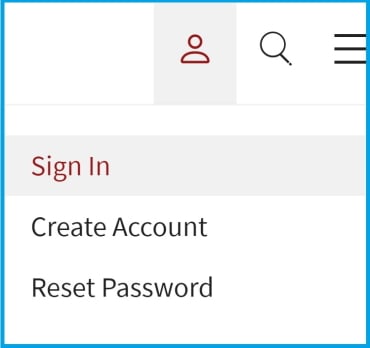
2.选择 "管理电子邮件首选项
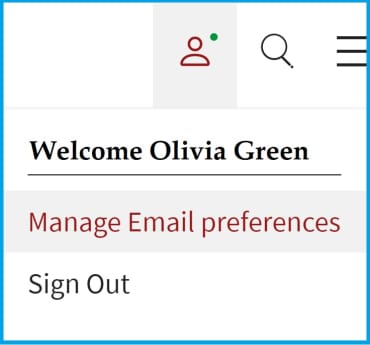
3.选中 "安全更新通知"
- 生效日期
- 最后更新
概述
Supermicro我们致力于维护产品与服务的安全性及完整性。本终止生命周期(EOL)安全政策阐述了我们如何管理已进入终止生命周期状态的产品的安全问题,确保透明度并协助客户规划升级与过渡方案。
什么是生命终结(EOL)?
当我们正式宣布不再积极开发、维护或增强产品或服务时,该产品或服务即被视为 "EOL"。
安全支持时间表
我们知道,从传统产品过渡需要时间。为了支持我们的客户
- 对于严重(9.0 - 10.0)和高度(7.0 - 8.9)的安全问题,将在 EOL 公告日之后的三 (3) 年内继续提供支持。
- 在此期间,我们将对报告的漏洞进行评估,并可能根据严重程度和影响发布补丁或缓解措施。
- 三年期限过后,将不再提供安全更新或调查。
例外情况
超出标准三年期限的扩展安全支持可通过单独协议获得。请联系Supermicro 具体方案。
联系我们
如对本政策有任何疑问或顾虑,请联系我们的安全团队:supermicro